
Privacy in America Now Starts With a VPN | A Brief Note on Threat Modelling and Lesser Evils
Category: thoughtsA 4 Minute Read
23 Mar 2017
Image by Michael Vadon

Today, the US Senate voted to scrap FCC privacy regulations that would have otherwise prevented internet service providers from selling a customer’s browsing history to third party advertisers. As The Verge explains:
The privacy rules, passed last year by the FCC, required internet providers like Comcast, Verizon, and AT&T to get each customer’s permission before sharing personal information like which websites they visit. But internet providers want to be able to sell that data and use it to target ads, so they’ve been vocal about opposing the rules since around the time President Trump took office.
With these rules now undone, this means that if you live in the US, your ISP can now legally watch every website you visit (and if you’re not using HTTPS then every page of every website visit), and then sell that information to advertisers, whole hog. This is a problem.
Fortunately, there are several workarounds (I dare not say solutions because the proper solution is proper regulation). Of course, these include Tor, I2P, and FreeNet, to name a few. Another workaround, and the one that I believe most of those impacted will deploy, is a VPN.
VPNs, however, are quite controversial. Following the Senate’s vote, popstar-infosec-expert Swift on Security immediately came out with the following tweet that completely dismisses them:
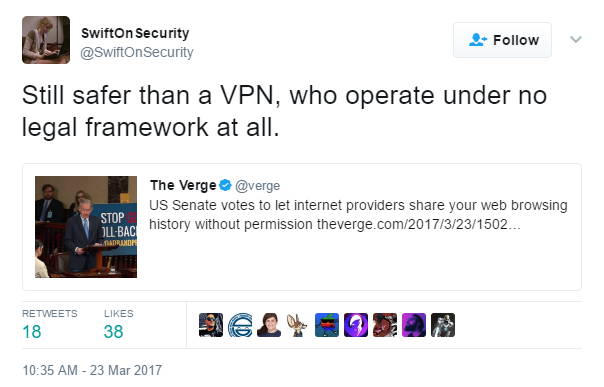
Indeed, it is true. VPNs typically operate in a legal gray area, if not a black hole. Moreover, there is no way to verify that they don’t violate your privacy, regardless of whether that is by sending it to the NSA or selling it to an advertiser.
On the other hand, the VPN market is so crowded that reputation means absolutely everything. A single bad verifiable story could run a VPN company into the ground. That is not to say that no VPN company would ever betray a promise of privacy, but only that doing so would entail significant risk should a disgruntled employee go public. Perhaps I am being naïve, but I do not believe that most well-reputed VPN companies would violate their promise of privacy and take on this risk. Certainly, some will, but most will likely not.
As far as ISPs are concerned, they have never made such a promise of privacy, and most of their customers likely do not care enough about privacy to affect their bottom line, especially given the lack of competition in the American ISP market. Surely they will face some backlash, but long-term losses will likely be minimal compared to the gains made by selling consumer information.
If you share this belief, then we are met with a decision we must make: who do we trust more, our ISP who is almost certainly selling our data, or a VPN who is only possibly selling our data? I think the answer is obvious. As it stands, reputable (such as NordVPN, Private Internet Access, and Mullvad) VPNs are a lesser evil as compared to American ISPs.
What actions we take after making this decision is dependent on our threat model. For most people, having their browsing history tracked is more of an ethical than practical decision; their desire for privacy is not because of a direct threat to their personal safety but rather a sense of unease knowing that they are in a database somewhere and maybe that could in the future be disadvantageous to them. With this in mind, commercial VPNs seem like a fair trade-off for most of their users between risk of privacy violation and usability/speed. In fact, I would go on to suggest that if VPNs suddenly stopped being an option, most of their users wouldn’t move to something more secure, like Tor or I2P, but instead to nothing at all, simply accepting the surveillance their ISP conducts on them.
But, for those that are more technically inclined, setting up their own VPN using a cheap VPS in Switzerland, for example, might be a more suitable workaround. Then, of course, there are those that only trust Tor, which has its own quirks when it comes to threat modelling.
Before rambling too much, I’ll end with this. The point of this post is two-fold. First, it is to quickly update you on the fact that if you value your privacy and live in the United States then you need to start considering how you will protect your data from your ISP. Read the EFF’s introduction to threat modelling, and begin to understand what exactly it is you’re protecting and what you need to do to accomplish this.
Second, it is to remind everyone that your threat model is your own, and that the lesser of two evils might actually be a suitable workaround for the average individual. No single tool will work for everybody; each has its own trade-offs, whether that’s Tor (high anonymity but slow), I2P (customizable and secure but difficult to use), or commercial VPNs (only privacy by policy but fast and easy to use). In short, don’t immediately come down on someone for using a commercial VPN without asking them a simple question: ‘what’s your threat model?’
