
ZeroNet | Introduction & Setup Tutorial
Category: darknetsA 6 Minute Read
03 Mar 2017
Image By NASA Goddard Space Flight Center

The ability to host hidden services is the hallmark feature of both Tor and I2P. For those that haven’t ventured into ‘the darknet’, hidden services are essentially websites that can’t be seen on the regular internet, are often run by anonymous operators, are end to end encrypted, and, because of these features, are very hard to censor. The only problem is that hidden services are, more often than not, terrible.
This is true for a few reasons. First, they’re usually lacking severely in the graphic design department, often resembling a Geocities page from 2001. Second, they’re often in a constant state of flux, wavering between working perfectly and not responding for hours at a time. Finally, when they are online, they. Are. Slow. Good luck downloading any site that is over a few megabytes in size.
This is looking like it could change very soon, however. With three heaping cups of BitTorrent tech, a splash of bitcoin crypto, and a table spoon of ingenuity, ZeroNet offers a solution to hidden services that drastically increases both their speed and reliability (unfortunately our eyes won’t stop bleeding soon).
How Zeronet Works
In essence, Zeronet is BitTorrent thrown at the problem of web hosting. Typically, hidden services run off a single server, which also functions as a single point of failure. When that server goes down, the site becomes inaccessible for everybody. When that server gets lots of traffic, the site becomes slower for everybody.
BitTorrent, on the other hand, utilizes a peer-to-peer system that drastically increases the reliability and speed of file sharing. Because of the fact that a given torrent might have 40 people sharing it, when a single server/user disappears or drops in bandwidth, there are 39 more to keep it alive and fill in the gaps (which also makes censorship nigh impossible). Zeronet takes this idea and instead of using it only for file sharing, it uses it to distribute websites. Indeed, with Zeronet every website seamlessly becomes a torrent.
The way this works is that if, for example, you want to share your website over Zeronet, you would first create a private key and a public key (using the same cryptography as bicoin). The public key functions as the address or URL for your website. Anyone who has your public key will be able to find your site. When they do find your site, they’ll download it and begin sharing it with others automatically. In other words, they become a peer.
Of course, you don’t want random people to be able to edit your site before sharing it with others. This would let them completely deface your site, and add any content to it that they wanted. The private key is what protects against this. Every time you modify your site, you’ll need to use your private key to verify that the modifications did indeed come from you, the site owner. As long as that private key is kept safe and secret on your computer, only you will be able to modify your site.
When you do modify the site and verify it with your private key, your computer will begin sharing the new site. When this happens, peers will check to make sure that the modified version is actually newer than what they have, and that all the files in it have in fact come from the site’s owner (i.e. you). Finally, all the modified files will then be downloaded and immediately shared across the network. This happens extremely quickly, meaning that sites can also be built to automatically update the page as new information spreads, making applications like a Zeronet-style Twitter that updates tweets in real time as they flow across the peer-to-peer network possible.
If you have been paying attention, this doesn’t necessarily involve Tor or I2P. Zeronet actually operates over the clear net by default. However, it can easily be configured (and on Windows this involves just pressing a button) to operate on top of Tor (I2P integration is in the works).
One of the implications of this is that you could very easily create a website, share it over Zeronet using Tor, and if you ever went offline there would be a whole network of individuals to fill in for you. The flip side of this is that if you ever visit someone’s site but lose internet connectivity, you can still browse it offline, you just won’t get any updates until you’re back online.
Another implication is that when new users visit your site, Zeronet will automatically ask the torrent tracker for a list of people that it can download the site from, and instead of downloading it from just your computer through the often oh-so-slow Tor network, they’ll download it from several others as well. This makes load speeds run many times faster.
But Wait, There’s More
ZeroNet is still in its infancy and doesn’t have the widest selection of quality sites quite yet. However, the developers do have several services already up and running that are interesting in and of themselves. The first is ZeroName. ZeroName uses Namecoin to securely turn ugly looking public keys into a regular, human readable domain name ending with .bit. This is similar to how I2P turns its own ugly addresses into domain names securely, except it utilizes the magic of the blockchain to do so. Of course, this vastly simplifies navigating ZeroNet.
Another service is ZeroMail, which is essentially just an encrypted email service, similar to Bitmessage. While it doesn’t use the fancy routing that I2P-Bote boasts, it nevertheless functions a basic mail platform that allows you to send messages to other people. A key advantage here is that ZeroMail can utilizes its own .bit domain, which again frees you from needing to remember/store and verify long keys every time you send a message or distribute your mailing address.
ZeroID is a service that allows you to create an identity you can use across ZeroNet that is tied to your private key. This means that nobody can forge your identity unless they steal that private key. It also means that you don’t need to remember a password.
Finally, ZeroMe is basically Twitter/Facebook on Zeronet. It lets you either create an identity unique to just your ZeroMe account, or to use your ZeroID so that you can hold a common identity across ZeroNet platforms. On ZeroMe you can post text, images, as well as follow others, just as you would on Facebook or Twitter.
For links to each of these services, just check out the left-hand toolbar after you get ZeroNet up and running.
Installation & Setting Up Tor
Windows
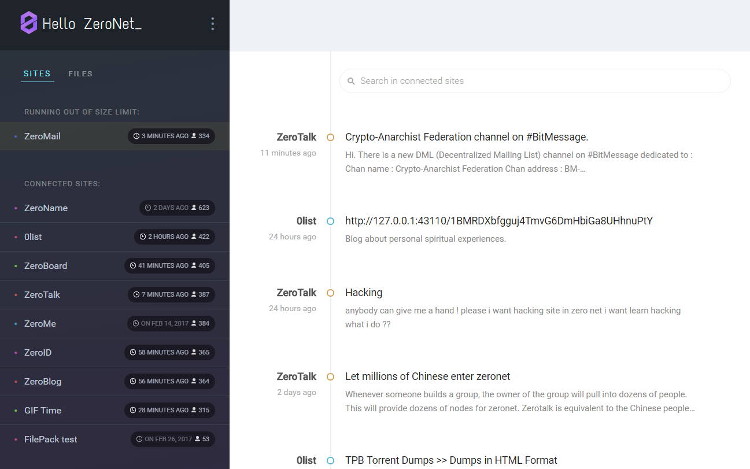
Installation on Windows is a very clean and easy process. Head over to zeronet.io and download and extract the installer. Then, just double click the ZeroNet.exe file, and it will open up the interface in your default browser (pictured below).
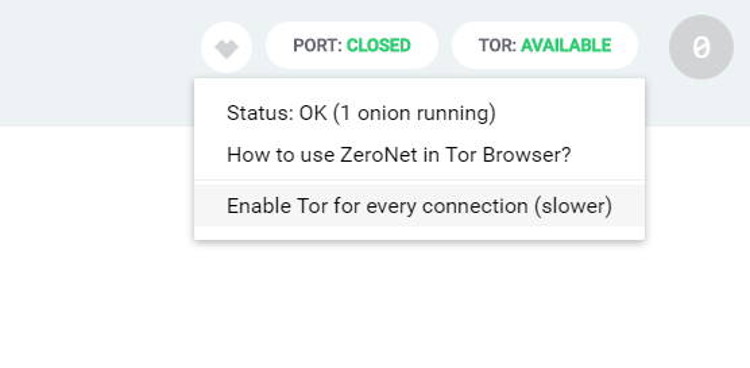
Setting up Tor is just as easy, as it comes bundled with ZeroNet for Windows. Once you’re in the interface, check the top right corner and click on the Tor button, shown below. Then, just click “Enable Tor for Every Connection”. This will slow things down, but ZeroNet is still relatively fast, and adding Tor will effectively hide your IP address from the network. After you’ve done this, click the three-dotted button in the top left of the interface, and select ‘Shut Down ZeroNet’. Tor will work for all the sites you visit only after you restart ZeroNet.
Linux
Installation on Linux is also fairly straightforward. Again, just head over to zeronet.io and download and extract the installer. Afterwards, open a terminal and cd into the ZeroBundle directory, before executing:
sh /ZeroNet.sh
ZeroNet will then open in your browser, but to get Tor working you need to do a bit of extra work, the first step being to install Tor onto your system. While ZeroNet’s documentation details this, I’ve added it here as well for simplicity. For Debian users, this means:
sudo apt-get update
sudo apt-get install tor
Next, you’ll need to modify the tor configuration file
sudo nano /etc/tor/torrc
Uncomment the lines where it says:
Control Port 9051
CookieAuthentication 1
Save and exit the editor, before modifying a quick account permission:
usermod -a -G debian-tor [yourlinuxuser]
Finally, reboot your system, rerun ZeroNet, and Tor should be working. To get ZeroNet to use Tor on every site, do just as the Windows users did and click the Tor button on the top right of the interface, select “Enable Tor for Every Connection”, and then restart ZeroNet.
Tor Browser
While you might be using Tor for routing, it is recommended that to achieve strong anonymity you should install the Tor Browser itself and use that to browse ZeroNet. The reason for this is that while your IP is still hidden by Tor, you can still be tracked through techniques such as browser fingerprinting, which the Tor Browser specifically protects against.
To do this, head over to torproject.org and download, install, and run the Tor Browser. Then, in the URL bar go to:
about:preferences#advanced
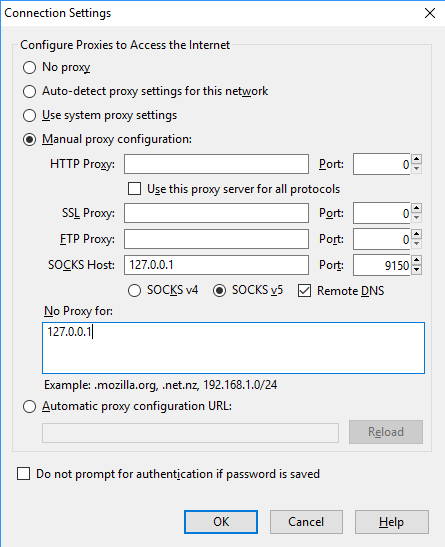
Go to the Network tab, Settings, and then set No Proxy For: 127.0.0.1, as shown below. With those pieces in place, you’re good to start browsing ZeroNet! Click here to get started with the ZeroNet home page.
